- Posted By: freeproject
- Comments: 0
- Posted By: freeproject
- Comments: 0
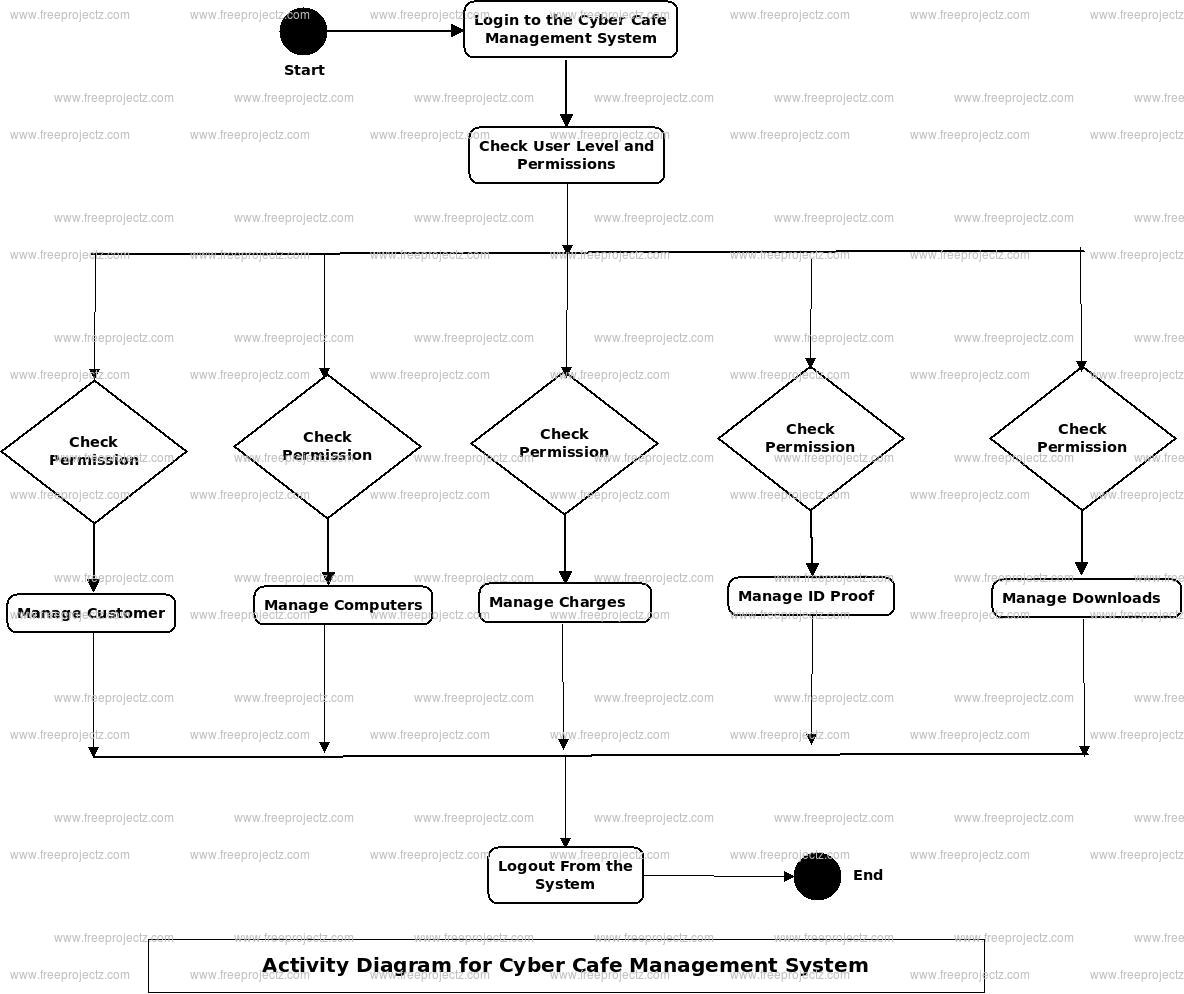
Cyber Cafe Management System Activity Diagram
This is the Activity UML diagram of Cyber Cafe Management System which shows the flows between the activity of Charges, Computers, Customers, Usage, ID Proof. The main activity involved in this UML Activity Diagram of Cyber Cafe Management System are as follows:
- Charges Activity
- Computers Activity
- Customers Activity
- Usage Activity
- ID Proof Activity
Features of the Activity UML diagram of Cyber Cafe Management System
- Admin User can search Charges, view description of a selected Charges, add Charges, update Charges and delete Charges.
- Its shows the activity flow of editing, adding and updating of Computers
- User will be able to search and generate report of Customers, Usage, ID Proof
- All objects such as ( Charges, Computers, ID Proof) are interlinked
- Its shows the full description and flow of Charges, Usage, ID Proof, Customers, Computers
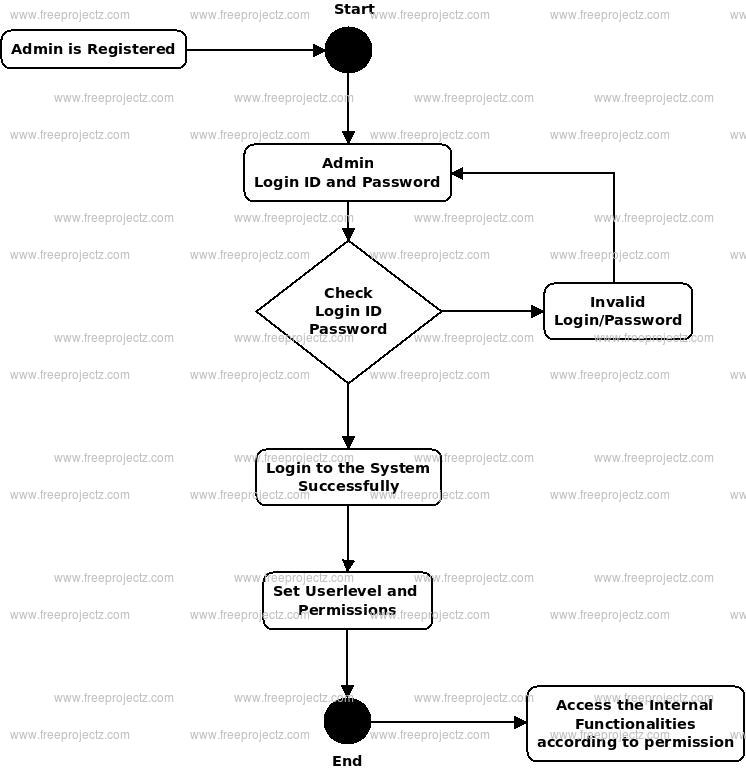
Login Activity Diagram of Cyber Cafe Management System:
This is the Login Activity Diagram of Cyber Cafe Management System, which shows the flows of Login Activity, where admin will be able to login using their username and password. After login user can manage all the operations on Customers, Charges, Computers, ID Proof, Usage. All the pages such as Computers, ID Proof, Usage are secure and user can access these page after login. The diagram below helps demonstrate how the login page works in a Cyber Cafe Management System. The various objects in the ID Proof, Customers, Charges, Computers, and Usage page—interact over the course of the Activity, and user will not be able to access this page without verifying their identity.
- Posted By: freeproject
- Comments: 0
Cyber Cafe Management System Class Diagram
Cyber Cafe Management System Class Diagram describes the structure of a Cyber Cafe Management System classes, their attributes, operations (or methods), and the relationships among objects. The main classes of the Cyber Cafe Management System are Computers, Customers, Charges, ID Proof, Downloads, Usage.
Classes of Cyber Cafe Management System Class Diagram:
- Computers Class : Manage all the operations of Computers
- Customers Class : Manage all the operations of Customers
- Charges Class : Manage all the operations of Charges
- ID Proof Class : Manage all the operations of ID Proof
- Downloads Class : Manage all the operations of Downloads
- Usage Class : Manage all the operations of Usage
Classes and their attributes of Cyber Cafe Management System Class Diagram:
- Computers Attributes : computer_id, computer_customer_id, computer_price, computer_company computer_type, computer_description
- Customers Attributes : customer_id, customer_name, customer_mobile, customer_email, customer_username, customer_password, customer_address
- Charges Attributes : charge_id, charge_customer_id, charge_amount, charge_type, charge_description
- ID Proof Attributes : id_proof_id, id_proof_customer_id, id_proof_name, id_proof_type, id_proof_description
- Downloads Attributes : download_id, download_title, download_type, download_description
- Usage Attributes : usage_id, usage_nmae, usage_type, usage_description
Classes and their methods of Cyber Cafe Management System Class Diagram:
- Computers Methods : addComputers(), editComputers(), deleteComputers(), updateComputers(), saveComputers(), searchComputers()
- Customers Methods : addCustomers(), editCustomers(), deleteCustomers(), updateCustomers(), saveCustomers(), searchCustomers()
- Charges Methods : addCharges(), editCharges(), deleteCharges(), updateCharges(), saveCharges(), searchCharges()
- ID Proof Methods : addID Proof(), editID Proof(), deleteID Proof(), updateID Proof(), saveID Proof(), searchID Proof()
- Downloads Methods : addDownloads(), editDownloads(), deleteDownloads(), updateDownloads(), saveDownloads(), searchDownloads()
- Usage Methods : addUsage(), editUsage(), deleteUsage(), updateUsage(), saveUsage(), searchUsage()
Class Diagram of Cyber Cafe Management System :

- Posted By: freeproject
- Comments: 0
Cyber Cafe Management System Component Diagram
This is a Component diagram of Cyber Cafe Management System which shows components, provided and required interfaces, ports, and relationships between the Downloads, Computers, Usage, Charges and ID Proof. This type of diagrams is used in Component-Based Development (CBD) to describe systems with Service-Oriented Architecture (SOA). Cyber Cafe Management System UML component diagram, describes the organization and wiring of the physical components in a system.
Components of UML Component Diagram of Cyber Cafe Management System:
- Downloads Component
- Computers Component
- Usage Component
- Charges Component
- ID Proof Component
Featues of Cyber Cafe Management System Component Diagram:
- You can show the models the components of Cyber Cafe Management System.
- Model the database schema of Cyber Cafe Management System
- Model the executables of an application of Cyber Cafe Management System
- Model the system's source code of Cyber Cafe Management System

- Posted By: freeproject
- Comments: 0
Cyber Cafe Management System ER Diagram
This ER (Entity Relationship) Diagram represents the model of Cyber Cafe Management System Entity. The entity-relationship diagram of Cyber Cafe Management System shows all the visual instrument of database tables and the relations between Customers, ID Proof, Computers, Usage etc. It used structure data and to define the relationships between structured data groups of Cyber Cafe Management System functionalities. The main entities of the Cyber Cafe Management System are Computers, Customers, Charges, ID Proof, Downloads and Usage.
Cyber Cafe Management System entities and their attributes :
- Computers Entity : Attributes of Computers are computer_id, computer_customer_id, computer_price, computer_company computer_type, computer_description
- Customers Entity : Attributes of Customers are customer_id, customer_name, customer_mobile, customer_email, customer_username, customer_password, customer_address
- Charges Entity : Attributes of Charges are charge_id, charge_customer_id, charge_amount, charge_type, charge_description
- ID Proof Entity : Attributes of ID Proof are id_proof_id, id_proof_customer_id, id_proof_name, id_proof_type, id_proof_description
- Downloads Entity : Attributes of Downloads are download_id, download_title, download_type, download_description
- Usage Entity : Attributes of Usage are usage_id, usage_nmae, usage_type, usage_description
Description of Cyber Cafe Management System Database :
- The details of Computers is store into the Computers tables respective with all tables
- Each entity (Usage, Charges, Downloads, Customers, Computers) contains primary key and unique keys.
- The entity Charges, Downloads has binded with Computers, Customers entities with foreign key
- There is one-to-one and one-to-many relationships available between Downloads, ID Proof, Usage, Computers
- All the entities Computers, Downloads, Charges, Usage are normalized and reduce duplicacy of records
- We have implemented indexing on each tables of Cyber Cafe Management System tables for fast query execution.

- Posted By: freeproject
- Comments: 0
Cyber Cafe Management System Sequence Diagram
This is the UML sequence diagram of Cyber Cafe Management System which shows the interaction between the objects of Charges, Computers, Customers, Usage, Downloads. The instance of class objects involved in this UML Sequence Diagram of Cyber Cafe Management System are as follows:
- Charges Object
- Computers Object
- Customers Object
- Usage Object
- Downloads Object
Login Sequence Diagram of Cyber Cafe Management System:
This is the Login Sequence Diagram of Cyber Cafe Management System, where admin will be able to login in their account using their credentials. After login user can manage all the operations on Customers, Charges, Computers, Downloads, Usage. All the pages such as Computers, Downloads, Usage are secure and user can access these page after login. The diagram below helps demonstrate how the login page works in a Cyber Cafe Management System. The various objects in the Downloads, Customers, Charges, Computers, and Usage page—interact over the course of the sequence, and user will not be able to access this page without verifying their identity.
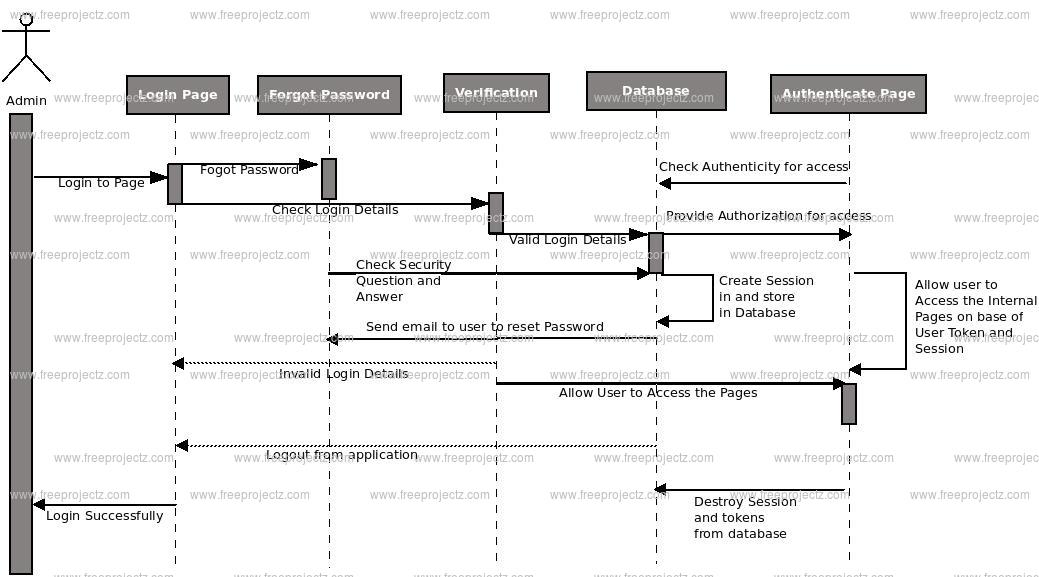
This is the UML sequence diagram of Cyber Cafe Management System which shows the interaction between the objects of Charges, Computers, Customers, Usage, Downloads. The instance of class objects involved in this UML Sequence Diagram of Cyber Cafe Management System are as follows:
- Charges Object
- Computers Object
- Customers Object
- Usage Object
- Downloads Object

- Posted By: freeproject
- Comments: 0
Cyber Cafe Management System Use Case Diagram
This Use Case Diagram is a graphic depiction of the interactions among the elements of Cyber Cafe Management System. It represents the methodology used in system analysis to identify, clarify, and organize system requirements of Cyber Cafe Management System. The main actors of Cyber Cafe Management System in this Use Case Diagram are: Super Admin, System User, Customer, Cafe Owner, who perform the different type of use cases such as Manage Computers, Manage Customers, Manage Charges, Manage ID Proof, Manage Downloads, Manage Usage, Manage Users and Full Cyber Cafe Management System Operations. Major elements of the UML use case diagram of Cyber Cafe Management System are shown on the picture below.
The relationships between and among the actors and the use cases of Cyber Cafe Management System:
- Super Admin Entity : Use cases of Super Admin are Manage Computers, Manage Customers, Manage Charges, Manage ID Proof, Manage Downloads, Manage Usage, Manage Users and Full Cyber Cafe Management System Operations
- System User Entity : Use cases of System User are Manage Computers, Manage Customers, Manage Charges, Manage ID Proof, Manage Downloads, Manage Usage
- Customer Entity : Use cases of Customer are Request for Internet, Check Internet Status, Check Time, Check Amount, Make Payment
- Cafe Owner Entity : Use cases of Cafe Owner are Assing Internet, Calculat Charges, Collect Payments
Use Case Diagram of Cyber Cafe Management System :




















